| Version 8 (modified by , 9 years ago) (diff) |
|---|
What is a signature and why should I check it?
The fact that you're using pidgin means that you have some level of trust in the authors, but it's not beyond the realm of possibility that someone else could make an "evil" patched version of pidgin which would steal your sensitive data without your knowledge.
When you download a file from the internet, unless you take additional steps, you don't have a good way of knowing if the file has been tampered with. If you were to somehow end up with the "evil" version instead of the official release, how would you know the difference?
This is where signatures come in - file signatures are very similar in principle to the idea behind signing both the back of your credit card, and a credit card receipt (pretending that the signature on a credit card receipt isn't trivially easy to forge for the purpose of this example). The signature can be used to verify that the file came from whom it was expected to come.
You probably have noticed that vendors frequently don't bother to compare the signature on the credit card receipt to the signature on the back of the credit card. When this happens, the vendor can't be confident that the person using the card is actually the card's owner. Similarly, if a file isn't signed, or you don't verify the signature on a signed file, you can't be sure that it came from where it was expected to come from.
Due to the nature of how signing works, an additional benefit is that when you verify the signature, you can be confident that nothing got corrupted during the download process - the file you verified is exactly as it was when it was signed.
Source Tarballs
The source tarballs (pidgin-$VERSION.tar.gz and pidgin-$VERSION.tar.bz2) are signed with GPG by one of the following people:
| Signer | Key Signature |
| Mark Doliner | 4C292FCC
|
| Ethan Blanton | 771FC72B
|
| Stu Tomlinson | A9464AA9
|
The signatures for the source tarballs (pidgin-$VERSION.tar.gz and pidgin-$VERSION.tar.bz2) are provided as separate $FILENAME.asc downloads from the same sourceforge download directory.
You can verify a tarball by downloading both the tarball and its corresponding .asc file:
gpg --verify $FILENAME.asc
If you haven't already imported the key that was used to sign the tarballs, you'll get a message about an unknown key when you attempt to verify; you'll need to import one of the above key signatures from a public keyserver (e.g. pgp.mit.edu):
gpg --keyserver pgp.mit.edu --recv-key $KEYSIGNATURE
You can read more about how the signing and verification works in the GPG Handbook.
Windows Installers
As of Pidgin 2.10.7, the various Windows binaries are signed in two ways.
- the installers and
pidgin.exeare signed using the Microsoft Authenticode signing mechanism by Daniel Atallah using a certificate with a thumbprint of one of the following:- Pidgin 2.10.7 - 2.10.9:
C5476901C3C63FABF54CEBA9E3F887932A9579B5 - Pidgin 2.10.10+:
45b37f151a113d5070036421370813b9fba5cb13- Note that these signatures use the SHA-256 algorithm, which Windows XP doesn't support (you can still use GPG to validate the package)
- Pidgin 2.10.7 - 2.10.9:
- all distributed packages (installers, debug symbols, binary zip file, gtk bundle zip file) are signed with GPG by Daniel Atallah (
DE890574).
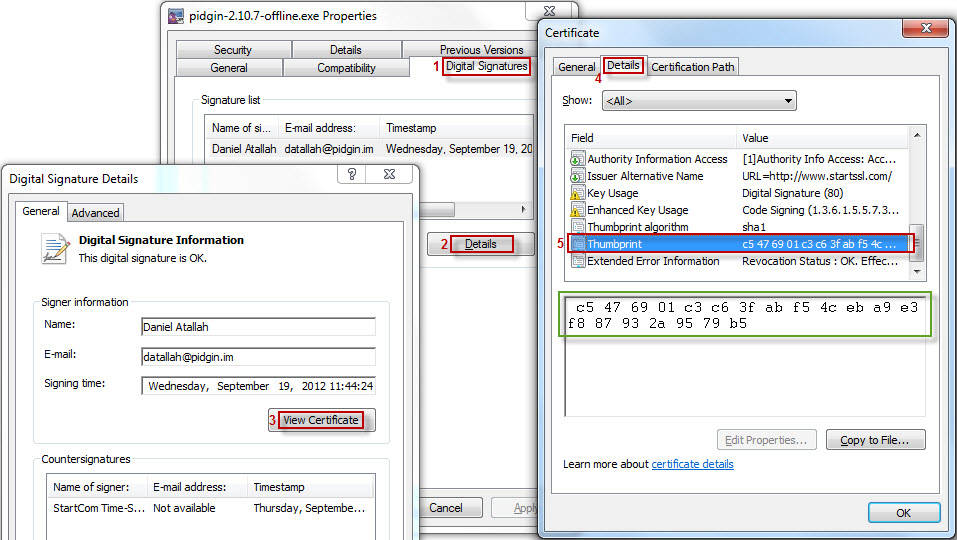
The authenticode signature can be verified most easily by using Windows Explorer to look at the Properties of the installer executable. In the "Digital Signatures" tab, you can look at the Details of the signature, "View Certificate", and compare the (case-insensitive, whitespace-insensitive) "Thumbprint" value in the "Details" tab to the value listed above.
Alternatively, authenticode the signature can be verified using Microsoft's signtool.exe utility (which, unfortunately, in order to obtain, requires that you install the at least parts of Microsoft Platform SDK).
GPG signatures can be verified on Windows in the same way as they're validated on other operating systems (see above). GPG binaries for windows are available - be sure to read the notes about how to validate your GPG binaries :)!
Attachments (1)
-
windows_cert_verify_thumbprint.jpg (97.6 KB) - added by 11 years ago.
Image showing the steps to verify the window signing certificate's thumbprint.
Download all attachments as: .zip